Malware devs watch the watchers: Google

A new arms race has opened up as browser developers find novel ways of detecting rogue sites and malware developers find unique ways of circumventing detection, according to a technical report (PDF) released by Google.
In order for browsers to avoid hostile sites, systems must be in place to detect web malware in the first place. According to the report, titled "Trends in circumventing web-malware detection", the four main methods used to detect malicious web content are virtual machine (VM) honeypots, browser emulation, reputation-based detection and signature-based detection.
However, malware developers are aware of the detection methods that researchers are using, and are taking measures to ensure that they fly below the radar.
VM honeypots
VM honeypots work by determining whether there are any differences in the operating system before and several minutes after a site has been visited. The advantage of such an approach is that unknown exploits and vulnerabilities may be detected; however, determining what triggered the attack may be difficult.
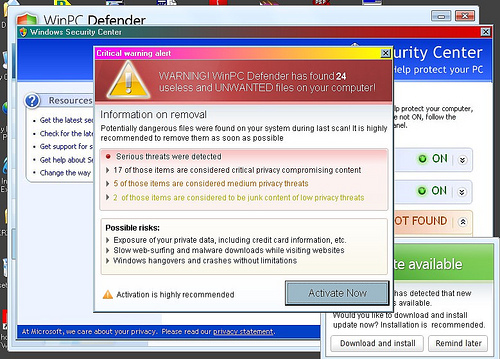
Any user interaction makes VM-based detection significantly more complicated to automate, meaning that attacks looking to cannily trick the user into downloading malware disguised as antivirus applications easily avoid detection.
Of the hostile sites, only 2 per cent of those examined in the study used this method to lure users to their doom, but the method's use had grown significantly in the past few years. According to the report, there was only one site distributing a fake antivirus in January 2007, but by September 2010, this number had increased to 4230.
In addition to the advantage of evading detection, the report said that it was likely that this growth was attributable to the monetisation ability of fake antivirus schemes.
Browser emulation
Browser emulation sees a security researcher set up a pretend browser that checks sites by parsing through HTML code for malicious code. The emulation also gives the researcher the ability to trace any JavaScript functions that are called, determine what line of code or event triggers an attack and monitor attempts to exploit known vulnerabilities in the browser.
Detection via browser emulation can be bypassed by smart malware developers, who can search for and determine the subtle differences between an emulator and a legitimate browser. As an example, Internet Explorer has a proprietary JavaScript engine that an emulator would not have access to, which would be more likely to use an open-source alternative.
Furthermore, once new vulnerabilities are made public, emulators need to be updated in order to detect them, resulting in a continual lagging period in which users are not protected and are likely to be vulnerable.
Reputation-based detection
Reputation-based detection involves flagging pages as unsafe, based on whether they include resources that are hosted on domains known to be malicious, and predicting which domains are likely to be suspicious based on the reputation of the hosting infrastructure.
Malware developers are also able to evade having their domains being classified as hostile by registering a significant number of them and setting up redirectors, some of which may only have a short lifespan. Of the 1.6 million distribution domains that Google observed over its collection period, about 330,000 had a lifespan of less than 10 minutes. The median lifespan of these redirection domains in 2007 was over one month, but, by October last year, it was down to two hours.
Further attempts to evade detection include setting up intermediary sites to form chains of redirection domains. While the report said that the median number of domains used in chains is about one or two domains, the longest chain it had seen from its data was 20 hops.
Signature-based detection
Signature-based detection is typically used by antivirus systems that scan payloads for known indicators.
Like browser emulation, signature-based detection requires the latest updates and heuristics, resulting in a vulnerable period where the antivirus is unable to detect zero-day exploits.
The report also said that malware creates techniques to hide within the code their malicious web content, which has a large impact on signature-based detection rates. When uncovering that code, the report observed better detection rates, in some cases by up to 40 per cent.
Due to the ease at which malware developers can circumvent each of the four most popular detection methods, the report said that none of them are effective in isolation. In order to have some level of competent detection, the report suggested the use of multiple types of detection. For example, the combination of VM-based detection and browser emulation would complement each other's strengths and weaknesses.
However, despite a multifaceted approach, the report admitted that malware developers have a trump card that they can play, which simultaneously defeats all four detection methods. It said that malware developers could actively choose to not deliver payloads to IP ranges belonging to detectors in what it calls IP cloaking. The report said that configuring a web server to do so would be quite easy, and one of the only methods for researchers to circumvent this would be to run detection systems from a different IP range following discovery of a range by malware developers.